
views
After the central government released a statement assuring that CoWIN is “completely safe”, cyber threat analysis company CloudSEK released its report stating that threat actors do not have access to the entire portal or the backend database.
But the analysis by the team of researchers has revealed that, as per their understanding, threat actors have access to various credentials belonging to health workers that they may have used to break into the CoWIN site and the data they have access to.
“Based on matching fields from Telegram data and previously reported incidents affecting Healthworker of a region, we assume the information was scraped through these compromised credentials. The claims need to be verified individually,” said CloudSEK.
The team also said: “On March 13, 2022, a threat actor on a Russian cybercrime forum advertised for compromised access on the Cowin Portal of Tamil Nadu region and claimed to have compromised the CoWIN database. Upon analysis, we discovered the breach was that of a health worker and not really on the infrastructure.”
Dark Web
In addition, the team stated that there are various healthcare worker credentials for the CoWIN site available on the dark web. This vulnerability, however, derives mostly from insufficient endpoint security protections deployed for healthcare personnel.
Minister of State for Skill Development and Entrepreneurship and Electronics and Information Technology Rajeev Chandrasekhar stated in a tweet, “It does not appear that Cowin app or database has been directly breached.” So the analysis from CloudSEK might be the answer to questions raised about an “indirect breach”.
Telegram Bot
It was reported earlier that the personal information of many Indians, including their Aadhaar and passport details, phone number, date of birth, and gender, were available on the Telegram app for a brief period of time.
A bot was working like a search engine, as it was sharing information, including the location where the vaccination was administered, and if someone’s phone number was given to it.
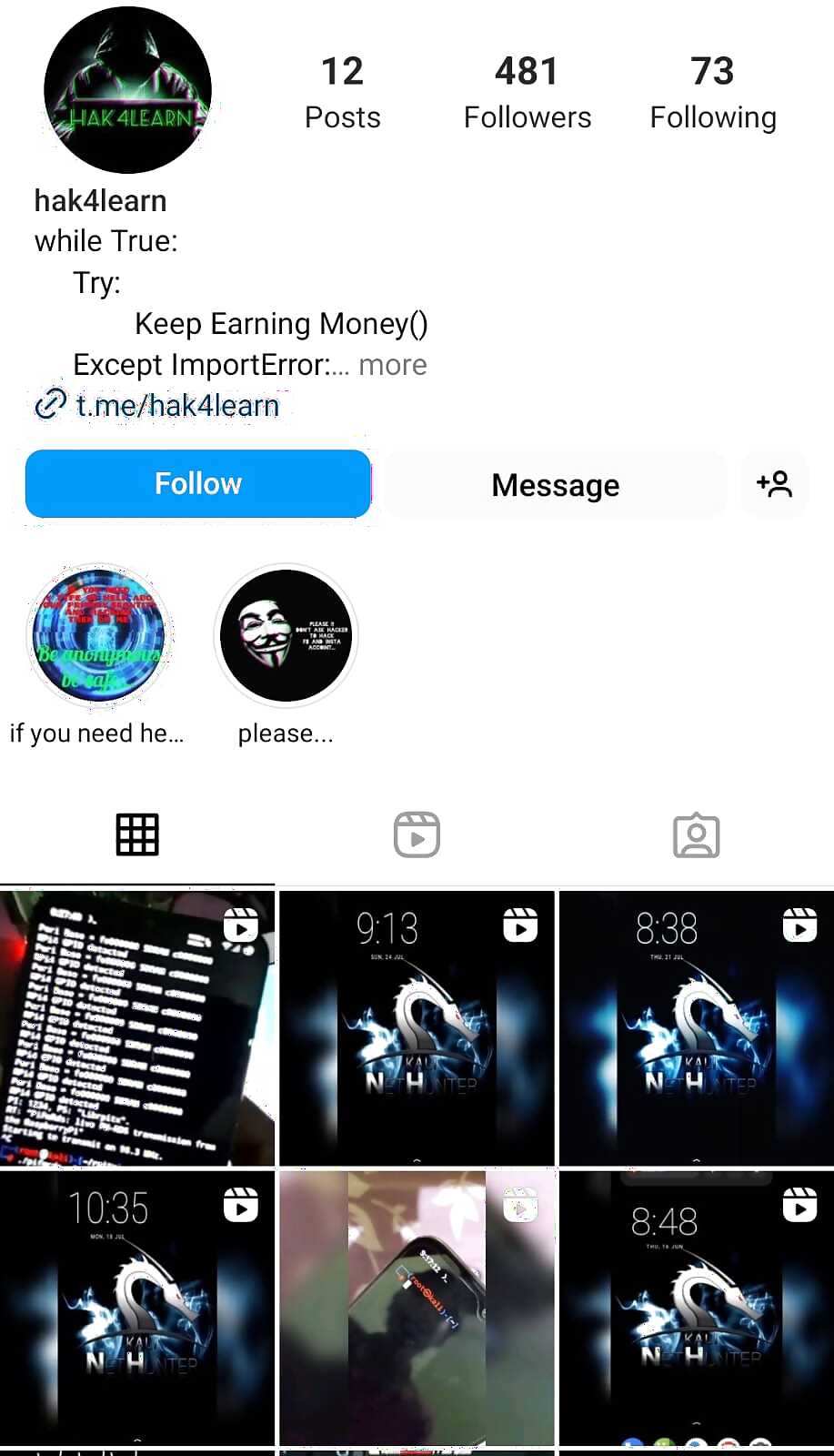
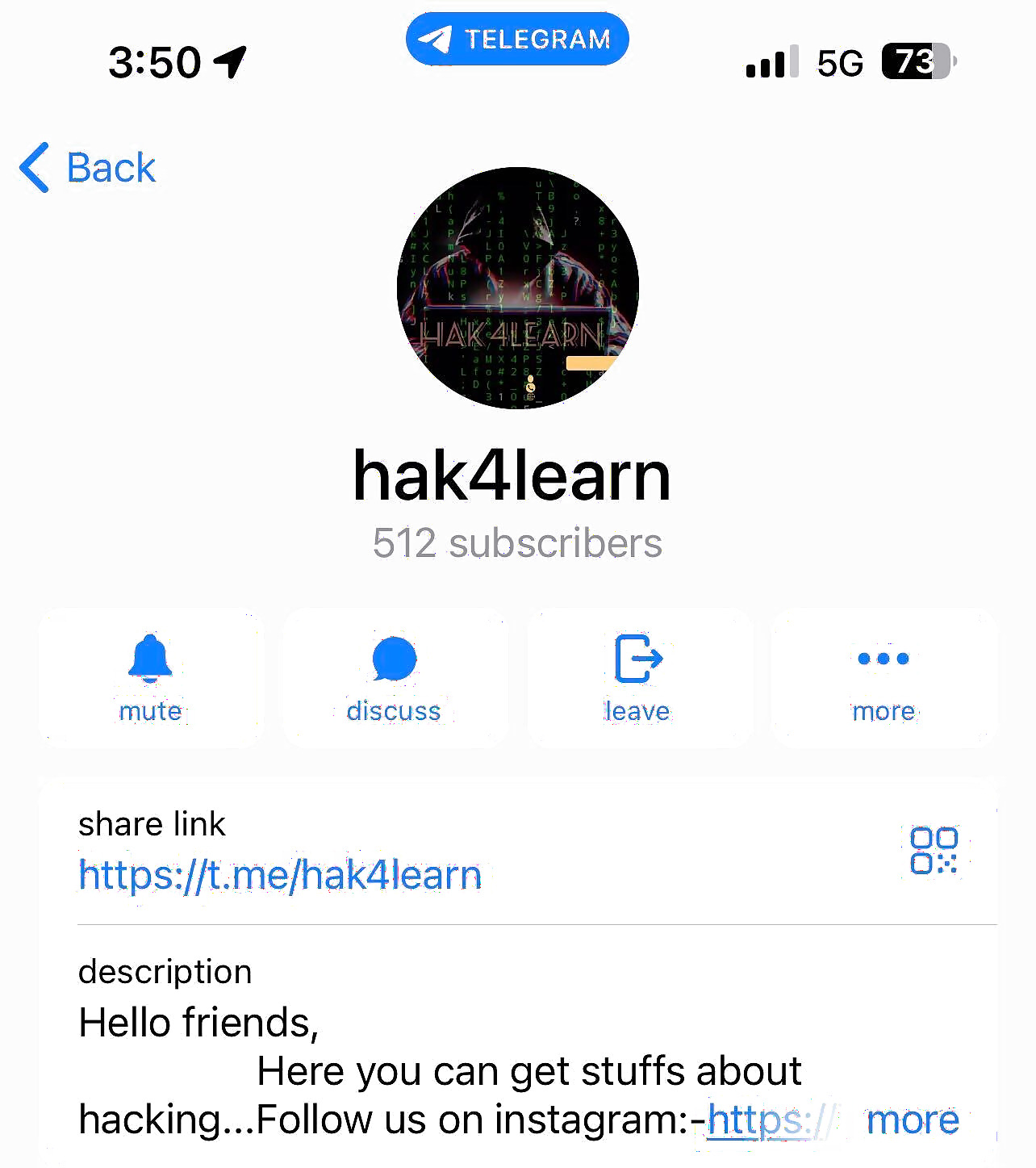
CloudSEK revealed that the bot was offered by a channel called hak4learn, which frequently shared hacking tutorials, resources, and bots for individuals to access and buy. Apparently, the bot, which is now inactivated, was initially open to everyone, but it was later upgraded to be exclusive to subscribers.
“The upgraded version of the bot provided personally identifiable information (PII) data, including Aadhaar card numbers, PAN card, voter ID, gender, and the name of the vaccination centre, based on the inputted phone number,” the report noted while sharing the screenshot of the Telegram channel.
It also said: “The real source of the Telegram bot is unknown, it is important to note that the bot had Version 1 offered that only displayed personal information based on Phone number. While the Version 2 claimed to be Truecaller bot that also contained personal information of the individuals.”
However, the channel, which launched on December 11, 2021, offers a wide range of Telegram bots, including a Truecaller bot for collecting location information based on phone numbers, an OTP bot, a UPI Recon bot, a Phishing page bot, and many more.
“The advertised post contains screenshots of the admin portal revealing the PII of people who have registered for COVID-19 vaccination drives. Exclusive Humint Analysis revealed the data belonging to the Tamil Nadu region and the actor claimed access to this single region’s centre at that moment,” the report added.
The team also found an active Instagram account, which is using the same name hak4learn. As per CloudSEK, the account is likely associated with the threat actor.


















Comments
0 comment